Getting Started with the Autonomous Kit for the Sphero RVR
Contributors:
santaimpersonator
Remote Access with SSH
Secure Shell (SSH) is a network protocol that allows users to remotely access the Raspberry Pi from another computer, through the WiFi network. Accessing the Raspberry Pi is a relatively simple process:
Suggested Tutorials:
For users who have never accessed a Raspberry Pi in a headless setup, please review this tutorial.
Headless Raspberry Pi Setup
Configure a Raspberry Pi without a keyboard, mouse, or monitor.
SSH Client Access
- To access the Raspberry Pi, users will need the IP address of the Pi. (*For users that used the SD card method, don't worry. The Raspberry Pi can still be accessed; however, only one Raspberry Pi can be powered at a time.)
- More information on determining the Raspberry Pi's IP address can be found on the Raspberry Pi Foundation's website.
- On the computer used to remotely access the Pi, pull up the SSH Client, Terminal, Linux Console, or Command Prompt (Windows 10 with October 2018 Update or later).
Use the following command to test if the Raspberry Pi can be accessed:
ping <IP Address>ping raspberrypi.local(if the SD card method was used)
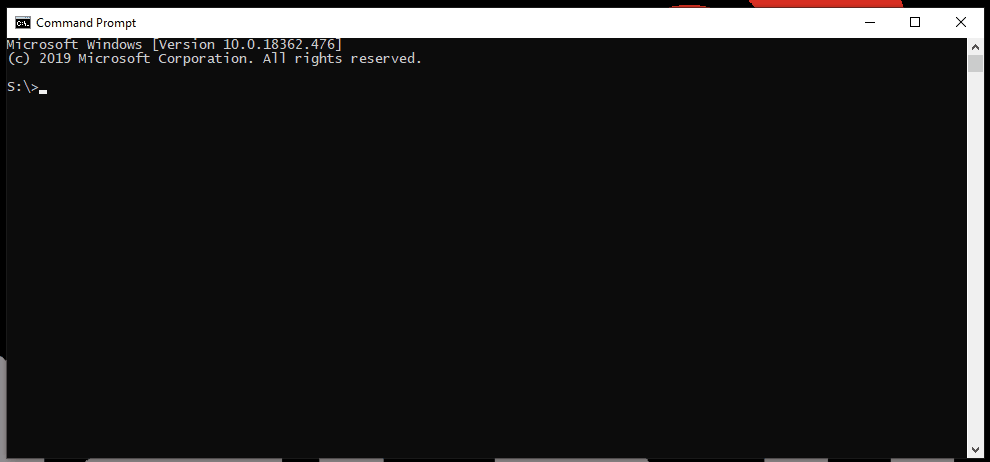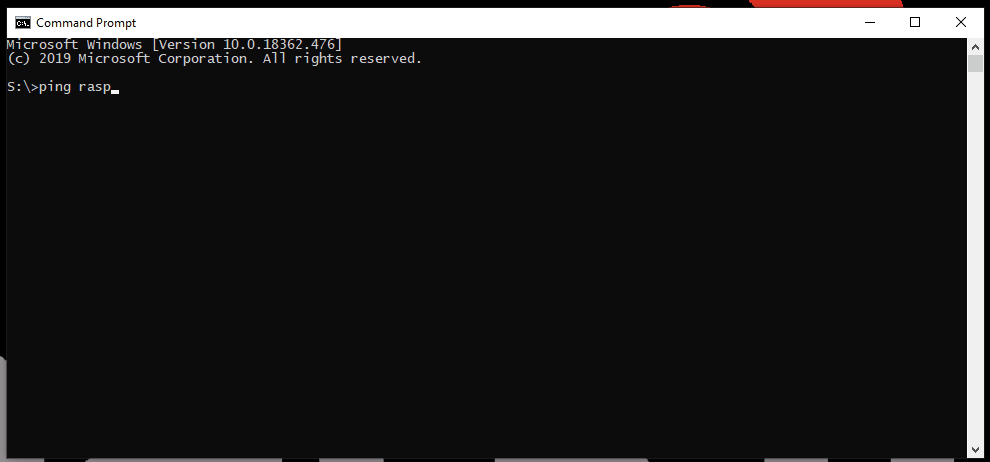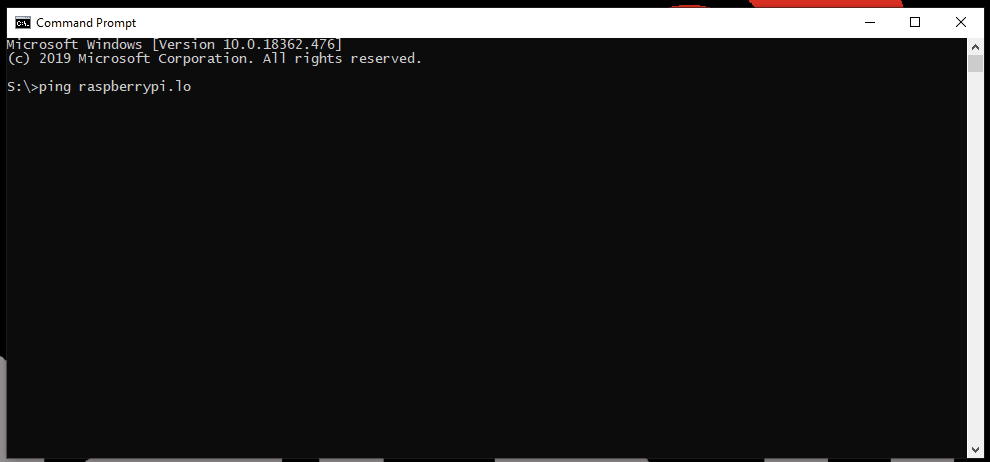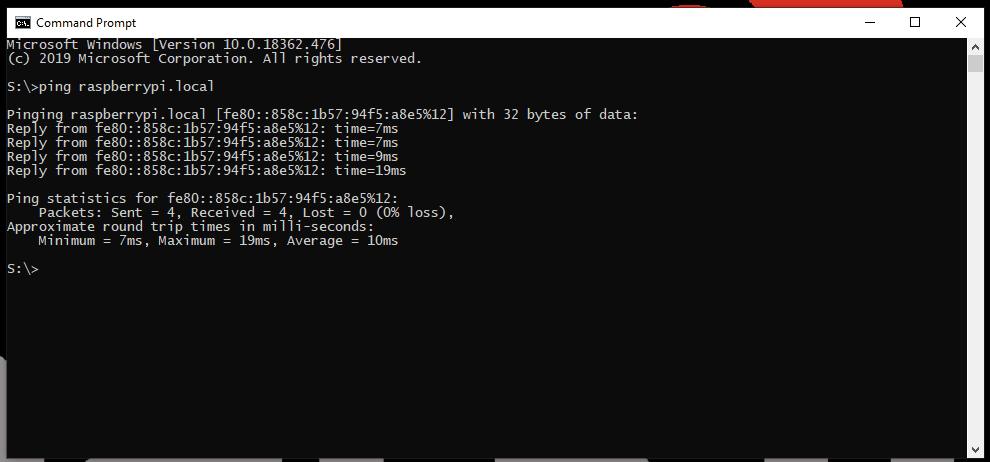
pingthe Raspberry Pi to confirm that is has connected to the WiFi network. (Click to enlarge)- If a connection is made, a print out of the response times will display. (If needed, press Ctrl+C to kill the process.)
To SSH into the Raspberry Pi, use the following command:
ssh pi@<IP Address>(piis the username of the account that will be accessed.)ssh pi@raspberrypi.local(if the SD card method was used)
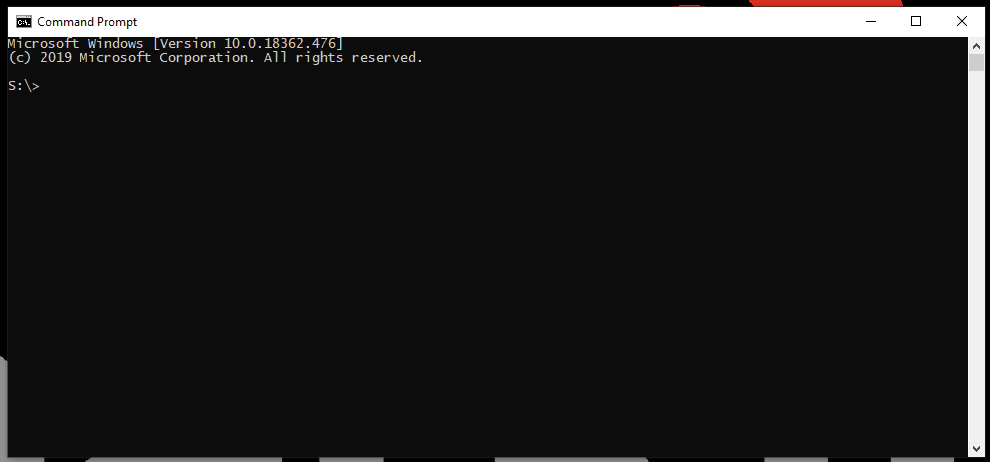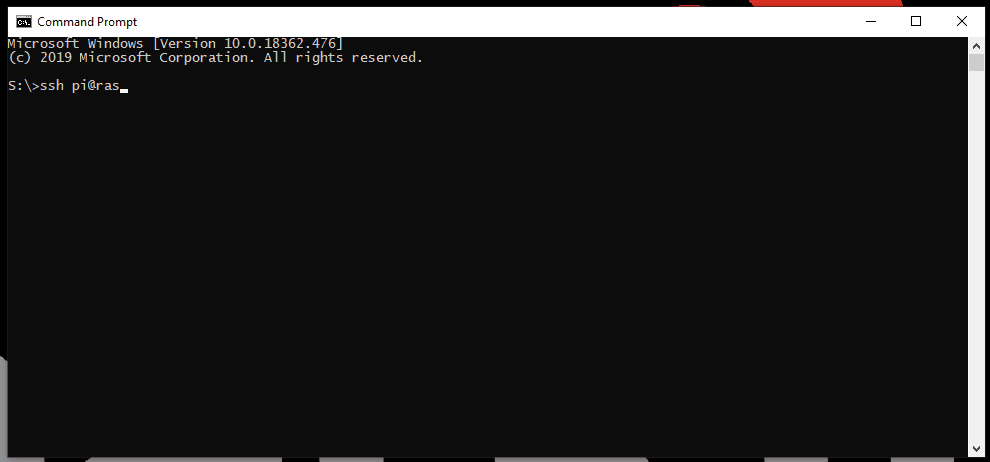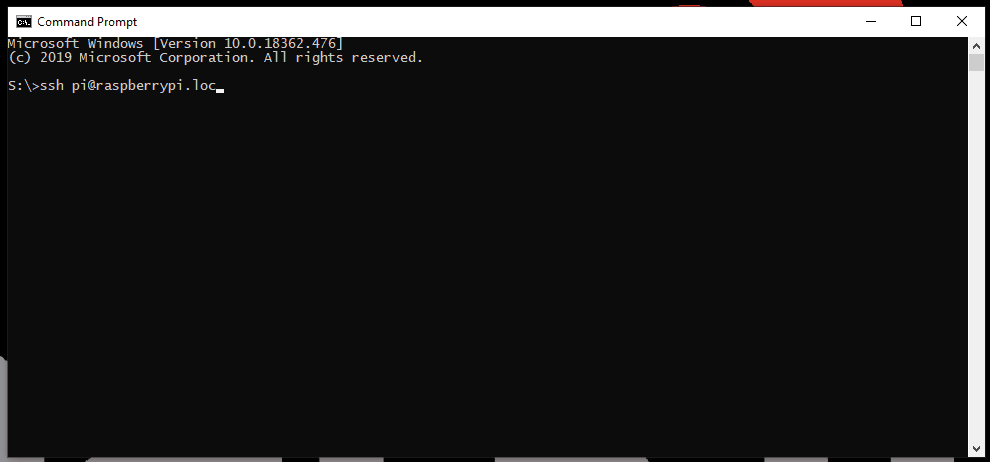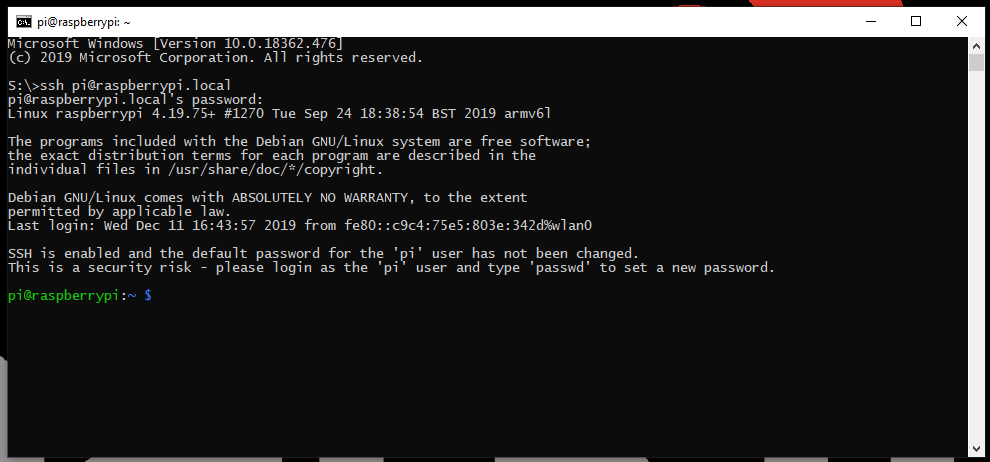
sshinto the Raspberry Pi, using the default credentials. (Click to enlarge)- The Raspberry Pi will prompt users for the password for the
piuser. The username and password are the default for the Raspberry Pi:- Username =
pi - Password =
raspberry
- Username =
(*More information on remotely accessing the Raspberry Pi through SSH can be found on the Raspberry Pi Foundation's website. Additionally, there also is information on other remote access methods.)