Gas Pump Skimmers
Components
Let's look a bit closer at each of the main components.
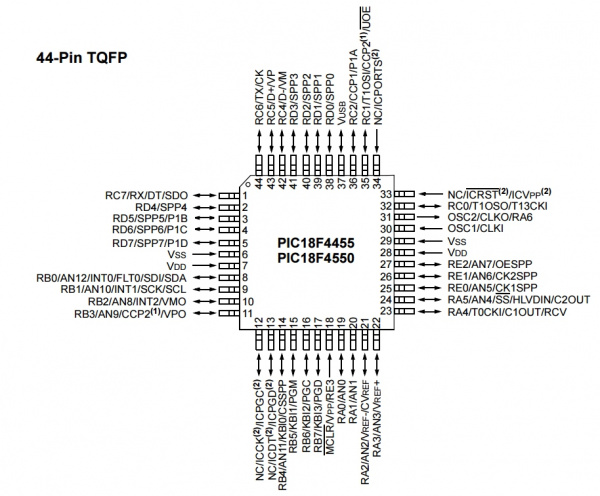
Microcontroller
The brain is a PIC18F4550 running at 8MHz and 3.3V. The 3.3V regulator has a single decoupling cap. A very basic configuration and could probably handle larger voltages like 12V without getting too hot.
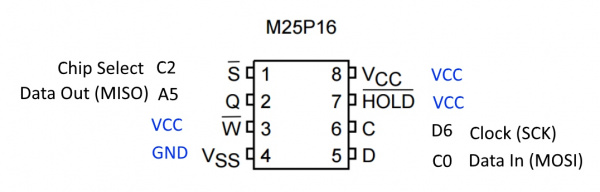
EEPROM
The IC labeled 25P16VP seems to be a NOR flash memory from ST/Micron with a full part# M25P16. Curiously, this part is being End-Of-Lifed (EOL). EOL notice is here dated December of 2016 with last shipment dates into 2021. Perhaps they are using this part because it is super common and/or super cheap. The EEPROM VCC is 3.3V which follows why the board runs at 3.3V (along with the 3.3V Bluetooth module).
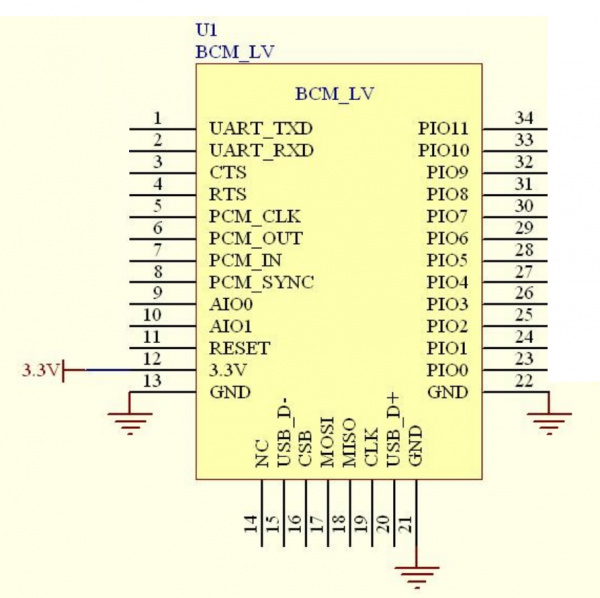
Bluetooth
Above is the recommended wiring of the module showing various pin connections. Toning out the connections to the module, everything is pretty standard and expected. PIO11 on the skimmer is curiously tied to GND with a 10K. There is an LED on PIO8. Here is a good breakdown of all the various Bluetooth module revisions from the HC-01 company.
Querying the module over the air we found the Bluetooth module has all the default settings in place. The designers of the skimmer never took the time to modify the settings:
- Baud rate = 9600
- Connection Password = 1234
- nl/cr line endings not required
- AT commands are required to be in uppercase
- Firmware version = hc01.comV2.0
- Name = HC-06
- No parity
- SLAVE mode
Did you get that? All three devices we found have the defaults in place. This means a few things:
- The module broadcasts its ID as HC-06 so we can detect them easily
- The password is 1234 so we can connect to them easily
Astute readers see where we are headed...
Initially this blew my mind. If I were to design a bluetooth skimmer I would program the module to NOT broadcast its ID, I would change the ID to something only I knew, and I would change the password from 1234 (headsmack). I would then create an app that knew the IDs of my various bluetooth IDs and connect to them privately (without publicly broadcasting their IDs). But then a few things struck me:
- These devices are cheap. The BOM (bill of materials) is less than $4. That puts an estimated retail price of this device at $10.
- While the SMD build quality is professional, the soldering of the ribbon (the gray cable that connects to the credit card reader) is horrendously bad indicating the perpetrator has very little experience with soldering and probably zero experience with electronics.
Years ago it took someone with knowledge and skills to build a credit card skimmer. Now criminals are buying these off the shelf with very little knowledge and slapping them together. It's basic user design theory: when your customer is not so smart make it idiot proof so they don't contact you for support. The designers of this skimmer were smart, it's better to make these devices easy to connect to than to add a layer of security. What's the worst that could happen? The device is detected and removed from the pump. Meanwhile, 10 more have been deployed for a total cost of $100.